Ransomware in a nutshell is the type of malware that encrypts all your files on a computer. Pay a ransom and MAYBE you will get your data back.
Statistics for 2023 are not good. At all. Ransomware attacks gained momentum with a more than 50% increase compared to 2022. Check if your backups are in place and let’s dive into the world of ransomware campaigns. We will take a closer look at numbers in 2023, discuss the topic of ransom payments, and consider what future is waiting for us.
What do statistics say?
Cyberint Team did a great job publishing an analysis of the 2023 ransomware landscape. Here is an infographic that sums up key things in this topic.

The most active ransomware group
LockBit maintained the 1st position as the most active ransomware group with a contribution to 24% of all ransomware attacks in 2023. LockBit targeted the USA (400 attacks), the UK (58 attacks), and France (51 attacks).
The most often targeted sectors
Business services, retail and manufacturing are the leading industries in terms of ransomware targets.
Exaples of the biggest attacks in 2023 targeting some of the industries included in top 10:
Government sector: The City of Dallas https://www.sangfor.com/blog/cybersecurity/dallas-ransomware-attack-affects-30253-people
Manufacturing sector: Taiwan Semiconductor Manufacturing Company https://therecord.media/foxsemicon-ransomware-attack-taiwan
Healthcare sector: McLaren Health Care https://www.fiercehealthcare.com/providers/mclaren-health-care-confirms-ransomware-attack-says-its-investigating-threats-release

The year 2024 started with new attacks like ransomware campaign targeted Coop, one of the largest retail and grocery providers in Sweden. Link: https://securityaffairs.com/156709/cyber-crime/cactus-ransomware-coop-sweden.html
Cybereason report revealed the list of industries that are most eager to paying the ransom.
Construction (74%)
Tech firms (51%)
Energy, oil and utilities (43%)
IT (around 33%)
Retail (around 33%)
Business and Professional Services (around 33%)
Government (18%)
Link: https://www.cybereason.com/blog/ransomware-which-industries-are-most-likely-to-pay
There is a distinct coleration with top sectors targeted by ransomware groups and top industries that pay the ransoms.
Top countries attacked by ransomware
The top 5 countries are maintaining the leading positions. Worth mentioning, that in 2022, Russia was 10th, but in 2023 India entered 10th place in the ranking.
TOP 10 COUNTRIES
1. USA (49% of all ransomware attacks)
2. UK
3. Canada
4. Germany
5. France
6. Italy
7. Australia
8. Spain
9. Brazil
10. India
Here is also a bunch of statistics from Sophos, where we can see that a big number of attacks are resulting in encryption which is considered a half of success in cybercriminals scenario. The second half is to get the money, but we will discuss it later as a separate topic.

Crypto changed the world of cybercrimes
These days, ransom payments are usually directed to cryptocurrency wallets controlled by the attackers. No matter how crypto-positive you are, we have to say it: cryptocurrencies opened new doors for cybercriminals.
This is actually one of the reasons why ransomware campaigns are emerging in recent years. There was never an easier way to get money without paying additional commissions, making it harder to detect and easier to travel with. It’s too good to be true? I forgot to add that in some countries you don’t have to pay any taxes from crypto. For example, Dubai has 0% personal income tax, which basically means that if you are a tax resident in Dubai, you won’t have to pay a single dollar.
Let’s travel back to the year 2019, the golden times for ransomware paid in Bitcoin. As we can read in Emisoft article.
Bitcoin accounted for about 98 percent of ransomware payments made in the first quarter of 2019, according to figures from ransomware recovery specialists Coveware. As a result, Bitcoin has become an inextricable part of the ransomware model.
We all know how volatile the crypto market is. But have you considered that some of the pumps and dumps may be a result of ransom payments? There is no hard data to be sure, however these charts say more than a thousand words.

Notable increase in Bitcoin price after WannaCry attack. Chart courtesy of CoinMarketCap. — Emisoft
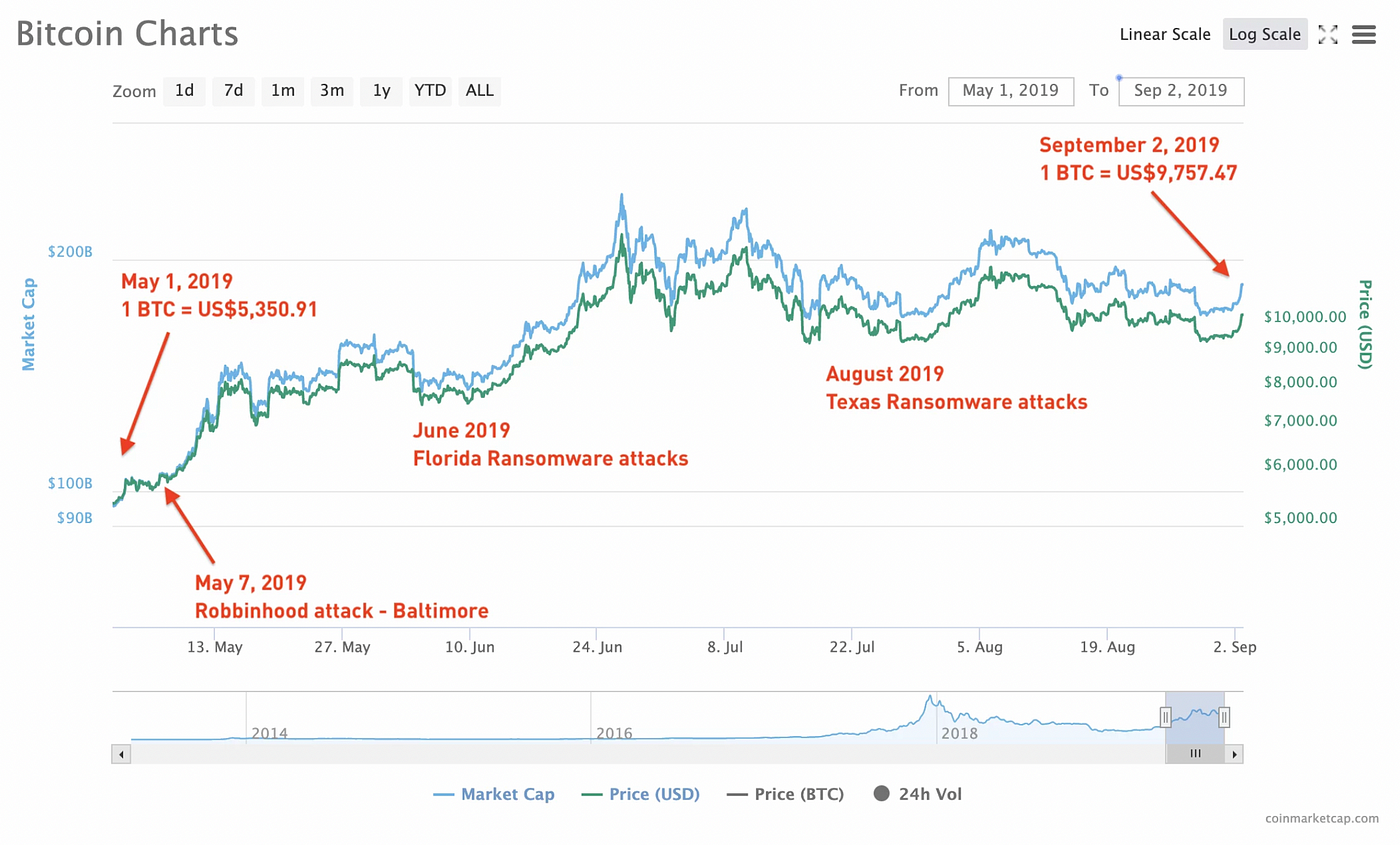
Rise in Bitcoin price from May 1, 2019 to September 2, 2019. Chart courtesy of CoinMarketCap. — Emisoft
As Chainlink claims: “Crypto payments to ransomware attackers hit $449.1 million in the first half of 2023, up $175.8 million from the same period last year.”
Alright, let’s switch back to the year 2024. Bitcoin is still a choice, however, the trend is actually moving away to cryptocurrencies such as Monero, Ethereum, or Zcash. Nowadays, they are much better than Bitcoin as they offer better security, privacy, anonymity and it’s hard to trace back transactions to a specific user or address.
Future of ransomware
Ransomware attacks are one of the most profitable and this is one of the reasons why it’s growing in intensity. One can say, that the future is bright for bad actors. What else is influencing the increased activity of ransomware groups? Here is a bunch of things to consider:
🔮 Ransomware attacks pivoted from blocking data to threatening to expose that data to the world, so companies are much more likely to pay the ransom.
🔮 The ransomware groups are developing more and more sophisticated attacks with well-prepared scenarios and a high level of successful completion, eg. Pikabot or DarkGate which are a more advanced version of Qakbot and are reaping the harvest in Q4 of 2023.
🔮 In the Dark Web we see the increase of Ransomware as a Service (RaaS), which is malicious software sold by cybercriminals to other hackers, providing them a whole package of all aspects of the attack including the software, the payment platform or the phishing operation. Running a ransomware campaign is becoming easier than ever.
🔮 With privacy cryptocurrencies like Monero or Zcash, it’s much easier to receive a ransom money and hide them from detection.
How to protect yourself?

Of course, a multi-layered security approach is always a good idea in such cases. Antivirus, firewalls, security awareness trainings for employees or the principle of least privilege to limit user access to the minimum is a standard these days, but let’s point out some of the most important things to consider.
Backups
Easier to say than do in most companies, but indeed this is one of the biggest protections we can provide to our business when ransomware attacks occur.
Often, backup of the whole infrastructure may be impossible. Then do frequent backups (daily, hourly) of the key points like GitHub/Bitbucket servers, Artifactory Registry server, databases servers, network configuration, etc.
Keep the backups in a safe place and the safest place is offline. However, you can consider cloud-based storage solutions with strong security controls as well. Use immutable storage solutions and encrypt the backups. Adding layers of security may not be the easiest task to do, but it’s sooo worth it! Just imagine, you may be a hero in your company one ransomware day!
Automation
Do not do anything on servers manually. Always keep properly configured and up-to-date automation scripts. With a good Terraform script you can create a new server in the cloud or Kubernetes cluster in a couple of minutes. With Ansible, Puppet or other tools you can quickly deploy the required configuration and secure the server. If you have to deploy applications on Kubernetes you should have proper automation to deploy tools like eg. ArgoCD and with this tool up and running you can quickly restore applications.
Network segmentation
Divide a computer network into smaller, isolated segments or subnetworks. If ransomware infects one segment of the network, we can prevent it to spread in other parts of infrastructure, becasue only one segments remain unaffected. The isolated segment prevents the ransomware from easily moving to other parts of the network. Place critical servers in segments with stricter access controls.
Patching
I know that’s boring, but do the upgrades! Keep your infrastructure up-to-date.
Email filtering and phishing trainings
Email thread hijacking or just standard phishing emails are common points of initial infection when it comes to ransomware attacks. A good example is the Pikabot, quite new and sophisticated malware used in ransomware campaigns. I will create a separate article discussing this malware and explaining how Pikabot is hijacking email threads.
Monitoring and logging
Monitor user's actions, unauthorized accesses, changes of important files, system logs, network traffic to detect unusual behavior and keep logs in a safe place.
Disaster recovery
Have a plan of recovery, make sure that each team knows what to do when the judgment day comes, and test if infrastructure can be restored as planned.
Summary
Ransomware is a big and important topic. Companies have to be prepared, as we’ve seen in statistics that in 2023 the number of lost revenue and business was significant.
Even if you will pay the ransom, you can’t be sure that data will be decrypted, so take care of backups in the first place. This can save the company.
At the same time, do what you can to prevent any malicious actions in the infrastructure. This is how you can protect the company and data of all of us which is one of the most valuable assets. Time to be a hero!